Patient Safety in the era of medical wearables and Healthcare IoT: Is new technology helping us to stay healthy or introducing risks?
Most of us now wear some form of fitness tracker and many hospitals and insurers are utilizing this 'personal health data' to supplement 'provider data' in our overall healthcare management. The volumes of healthcare data on each of us is staggering and is critical for our health management and overall well-being as patients. But what happens when that data is compromised, changed or deleted?
Like it or not healthcare delivery is more reliant upon technology today than ever before to diagnose, treat, observe, manage and monitor patients. A basic systems outage is enough to bring an entire hospital or clinic to its knees. Just look at what happened in the UK when Ransomware took down much of the NHS.
But our technology reliance is not just focused on IT systems any longer, there are a multitude of different Healthcare Internet of Things (HIoT) devices that we use to improve patient outcomes. All kinds of medical devices, from IMDs, to network connected pumps and scanners, to patient and nurse call systems, all of which are critical in direct patient care. And let’s not forget, that we cannot do without HVAC systems, elevators, power, water and other hospital building management systems, nearly all of which are now ‘smart’ and ‘connected’, often managed by business partners from thousands of kilometers away via the Internet.
What happens when these simple devices are attacked by extortionists and cyber-criminals? Does anyone even know how many HIoT devices are connected at each location, let alone when they were last patched and what security risks they pose to patients and to hospital IT systems? Just because they may be connected to an isolated network or VLAN doesn’t mean they are enclaved or segmented as far as security is concerned.
How can we gain greater visibility into what’s happening in our hospitals and become better prepared to defend ourselves from the next inevitable attack?
This was the subject of a recent presentation by the author to the HIMSS Australia Digital Health Summit in Sydney, NSW attended by many of the top thought leaders from across Australia, New Zealand and much of Asia.
Medical wearables could prove to be a valuable asset in the fight to prevent on the onset of disease. Diseases that by and large, are very expensive to treat. Primary care physicians have been urging us all for years for better preventative care, yet in many countries there is still a financial disincentive to go see the doctor or a specialist. In the United States where High Deductible Health Insurance pushes patients away from seeing their care team till they have met their often massive deductible before receiving any benefits, and in the developing world where the choice is sometimes to see the doctor or feed the family for a week. A trip to the doctor is also considered as being inconvenient and time consuming by many - even when there is no charge. What better then, than to automate the monitoring and well-being of patients using simple ubiquitous tools like an Apple Watch, or a Fitbit, something that avoids having to go see the doctor and actively engages patients in their own well-being.
An old adage claims “an apple a day keeps the doctor away”. It may originate from the days of scurvy and a general lack of fruits and vegetables in people's diet, but maybe there is some truth to the saying in today's hi-tech healthcare world.
A recent HIMSS survey claimed that 64% of surveyed patients might be more willing to wear an Apple Watch or a medical wearable if it means fewer trips to see the doctor.
A similar survey of hospital executives from HIMSS and AT&T found 47% of hospitals are providing wearables to patients with chronic diseases and are also conducting remote monitoring via in-home medical devices and smartphone apps.
Is this the future of regular health observation and maintenance? My Apple Watch already reminds me to get up and walk about several times a day when I have been busy sat typing or in meetings. Will future versions also tell me to cut down on my carbohydrate intake and to look for a less stressful job based upon my diet, activity levels, and heart rate?
The big question is, to what extent can consumer healthcare data be trusted as being accurate and not fudged to reduce health insurance premiums, and what should our health systems do to integrate that data into our medical record?
In Australia the existing My Health Record (MHR) initiative will see the roll-out of new functionality in 2020 for apps to connect into the MHR. Australians already have the ability to view their complete medical record (unlike most other countries) so the hope is that this should be the primary place where Aussies go to check their healthcare activity and well-being. Its precisely this type of public-private partnership that will lead to improved patient outcomes and reduced spending on chronic diseases, or so its authors claim with some justification.
Consumer wearables like Apple Watches and Fitbits are just some of a huge wave of Healthcare Internet of Things (HIoT) devices that are being used to monitor, manage, diagnose and treat patients. In all but the smallest critical access hospitals, HIoT devices already well-outnumber traditional IT computers and other systems. The challenge for the industry is how to manage and secure such a broad range of fairly dumb devices at a time when the healthcare industry is under an increasing number of cyber attacks.
How should Healthcare Executives go about securing their HIoT?
Managing traditional HIT assets like servers, laptops and workstations is a touch job in a healthcare environment because of a lack of standardization and the need to run so many different versions of operating systems and legacy applications. Trying to manage hundreds of thousands of discrete HIoT devices is near impossible without the right tools. The first problem is that most healthcare providers have no idea how many devices they own, rent, or have connected to their networks, nor the risks that each of them poses to patient safety or other network assets like the EMR, so this is where we need to start.
The following workflow may be useful as a guide:
What tools should you consider?
The good news is that this exercise is no longer a daunting labor-intensive manual process. There are first and second generation tools now available that can do this for you with varying levels of automation. Second generation tools like Cylera MedCommand, make extensive use of AI and ML to more thoroughly risk assess devices and seamlessly integrate to your existing asset management, GRC, SIEM and NAC technologies. Through a combination of passive and active security controls you can safely monitor and log traffic till you feel confident to turn your NAC to '
'active' or 'blocking' mode without having to worry that you may inadvertently isolate a device.
'MedCommand' provides clinical engineering and information security teams with a unified solution to manage and protect the entire connected HIoT environment including medical devices, enterprise IoT, and operational technology.
The solution is built on Cylera’s 'CyberClinical' technology platform, which incorporates machine learning, behavioral analytics, data analysis, and virtualization techniques. Cylera has partnered with leading healthcare providers, experts, and peers to develop one the most comprehensive and integrated HIoT security solutions available for healthcare.
Learn more about Cylera's innovative AI based approach to medical device and other HIoT endpoint management at https://www.cylera.com.
 |
| Medical Wearables. |
Most of us now wear some form of fitness tracker and many hospitals and insurers are utilizing this 'personal health data' to supplement 'provider data' in our overall healthcare management. The volumes of healthcare data on each of us is staggering and is critical for our health management and overall well-being as patients. But what happens when that data is compromised, changed or deleted?
Like it or not healthcare delivery is more reliant upon technology today than ever before to diagnose, treat, observe, manage and monitor patients. A basic systems outage is enough to bring an entire hospital or clinic to its knees. Just look at what happened in the UK when Ransomware took down much of the NHS.
But our technology reliance is not just focused on IT systems any longer, there are a multitude of different Healthcare Internet of Things (HIoT) devices that we use to improve patient outcomes. All kinds of medical devices, from IMDs, to network connected pumps and scanners, to patient and nurse call systems, all of which are critical in direct patient care. And let’s not forget, that we cannot do without HVAC systems, elevators, power, water and other hospital building management systems, nearly all of which are now ‘smart’ and ‘connected’, often managed by business partners from thousands of kilometers away via the Internet.
What happens when these simple devices are attacked by extortionists and cyber-criminals? Does anyone even know how many HIoT devices are connected at each location, let alone when they were last patched and what security risks they pose to patients and to hospital IT systems? Just because they may be connected to an isolated network or VLAN doesn’t mean they are enclaved or segmented as far as security is concerned.
How can we gain greater visibility into what’s happening in our hospitals and become better prepared to defend ourselves from the next inevitable attack?
This was the subject of a recent presentation by the author to the HIMSS Australia Digital Health Summit in Sydney, NSW attended by many of the top thought leaders from across Australia, New Zealand and much of Asia.
 |
| The Author addresses the HIMSS Australia Digital Health Summit in Sydney. Photo: HIMSS |
An Apple A Day Keeps the Doctor Away
An old adage claims “an apple a day keeps the doctor away”. It may originate from the days of scurvy and a general lack of fruits and vegetables in people's diet, but maybe there is some truth to the saying in today's hi-tech healthcare world.
Can an Apple on your wrist keep the doctor away?
A recent HIMSS survey claimed that 64% of surveyed patients might be more willing to wear an Apple Watch or a medical wearable if it means fewer trips to see the doctor.
A similar survey of hospital executives from HIMSS and AT&T found 47% of hospitals are providing wearables to patients with chronic diseases and are also conducting remote monitoring via in-home medical devices and smartphone apps.
Is this the future of regular health observation and maintenance? My Apple Watch already reminds me to get up and walk about several times a day when I have been busy sat typing or in meetings. Will future versions also tell me to cut down on my carbohydrate intake and to look for a less stressful job based upon my diet, activity levels, and heart rate?
The big question is, to what extent can consumer healthcare data be trusted as being accurate and not fudged to reduce health insurance premiums, and what should our health systems do to integrate that data into our medical record?
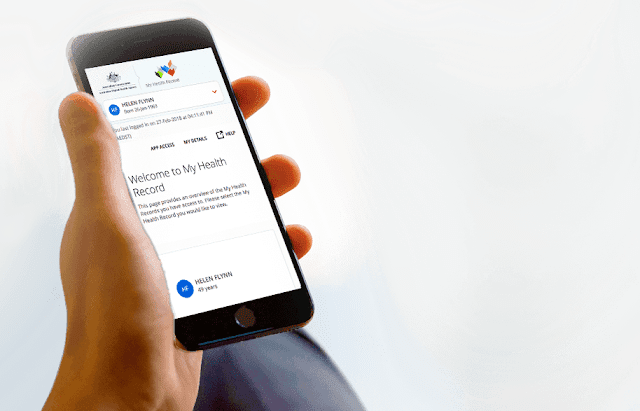 |
| Australia's My Health Record. |
In Australia the existing My Health Record (MHR) initiative will see the roll-out of new functionality in 2020 for apps to connect into the MHR. Australians already have the ability to view their complete medical record (unlike most other countries) so the hope is that this should be the primary place where Aussies go to check their healthcare activity and well-being. Its precisely this type of public-private partnership that will lead to improved patient outcomes and reduced spending on chronic diseases, or so its authors claim with some justification.
Consumer wearables like Apple Watches and Fitbits are just some of a huge wave of Healthcare Internet of Things (HIoT) devices that are being used to monitor, manage, diagnose and treat patients. In all but the smallest critical access hospitals, HIoT devices already well-outnumber traditional IT computers and other systems. The challenge for the industry is how to manage and secure such a broad range of fairly dumb devices at a time when the healthcare industry is under an increasing number of cyber attacks.
How should Healthcare Executives go about securing their HIoT?
Managing traditional HIT assets like servers, laptops and workstations is a touch job in a healthcare environment because of a lack of standardization and the need to run so many different versions of operating systems and legacy applications. Trying to manage hundreds of thousands of discrete HIoT devices is near impossible without the right tools. The first problem is that most healthcare providers have no idea how many devices they own, rent, or have connected to their networks, nor the risks that each of them poses to patient safety or other network assets like the EMR, so this is where we need to start.
The following workflow may be useful as a guide:
- Identify Assets – Most hospitals don’t know what they have!
- Risk Assess those HIoT Assets to NIST 800-30 or similar standards for compliance
- Identify CVEs and Zero-Days, any known patches and apply
- Beat up vendors for patches – some are better than others. Some are outright negligent.
- With hundreds of thousands of devices you will never be able to regularly patch them all!
- Identify and Map Legitimate Traffic Patterns – Ports, Protocols, IPs, etc.
- Construct a 'Zero Trust' white list of usual traffic patterns so that anomalous activities can be flagged and investigated or blocked
- Implement Micro-Segmentation as a compensating security control to protect patients and networks against devices that cannot be secured. Employ the Zero Trust white list to construct your NAC's Security Group Tags (SGTs) to automate protection.
What tools should you consider?
The good news is that this exercise is no longer a daunting labor-intensive manual process. There are first and second generation tools now available that can do this for you with varying levels of automation. Second generation tools like Cylera MedCommand, make extensive use of AI and ML to more thoroughly risk assess devices and seamlessly integrate to your existing asset management, GRC, SIEM and NAC technologies. Through a combination of passive and active security controls you can safely monitor and log traffic till you feel confident to turn your NAC to '
'active' or 'blocking' mode without having to worry that you may inadvertently isolate a device.
 |
| Cylera MedCommand. |
'MedCommand' provides clinical engineering and information security teams with a unified solution to manage and protect the entire connected HIoT environment including medical devices, enterprise IoT, and operational technology.
The solution is built on Cylera’s 'CyberClinical' technology platform, which incorporates machine learning, behavioral analytics, data analysis, and virtualization techniques. Cylera has partnered with leading healthcare providers, experts, and peers to develop one the most comprehensive and integrated HIoT security solutions available for healthcare.
Learn more about Cylera's innovative AI based approach to medical device and other HIoT endpoint management at https://www.cylera.com.






























