The Healthcare industry has undergone a dramatic technological transformation over the past decade. From our frustrating interaction with a provider’s voice menu systems before we can speak with a human, to script-reading near-useless overseas calls center staff that attempt to sort out medical billing problems, we have finally entered the digital era. Gone are the days of calling a provider, simply jump on the online provider web portal or open the mHealth app on your smartphone and get what you need – well almost!
Long gone are the days of fat manila files full of medical records that no one ever looks at (unless there is a problem) and welcome-in the days of the electronic medical record (EMR) with seamless interoperability across primary, secondary, and tertiary health providers. The EMR that prevents 10 different nurses asking you the very same question on each visit (yeh right!)
Gone are the days of the suited elderly stoic medical doctor with his leather doctor’s bag and personalized stethoscope, and in are the days of the guy or girl dressed in sneakers and scrubs who looks barely old enough to have graduated high school let alone medical school.
Today’s doctor’s office is now a showcase in medical technology. Absent are the bookshelves full of leather-bound medical journals and in their place are a gadgets, gizmos, and computers that all report dutifully to the almighty EMR. The average hospital bed has between 8 and 12 medical devices. The average ER or ICU bed can have upward of 30 connected medical devices per bed.
But the hospital room of today is not just stuffed with medical devices but the room itself is connected and smart. It turns off the lights when the room is empty, it knows when to tell the HVAC that it needs negative air pressure for (infectious patients) or positive air pressure for immune-compromised patients. It also contains CCTV cameras that display at the nearby nurse station to identify when a patient is in need of attention and a whole heap of patient telemetry systems that report all kinds of vitals to those whose job it is to know. Healthcare of the 2020s is now highly technology dependent and full of advanced equipment, and the pace of change is evolving at an almost exponential rate.
Medical technology has transformed our ability to quickly diagnose medical conditions, to treat ailments, often by non-invasive means, and to quickly restore a patient back to a fully functioning member of society. Genomics-based personalized medicine may one day prevent the onset of disease and the breakdown or wearing out of the body’s components, and this may render all of us perfectly fit and mentally healthy well into our nineties and for some, even beyond.
Digital interoperability between discrete medical, public health, insurance, and population health systems is now driving the meaningful exchange of public health information (PHI). So, when you need to see a doctor while on vacation hundreds of miles or kilometers away from your home, that doctor will have access (with your permission) to your complete medical records and be able to prescribe the best possible course of treatment for you.
In Europe a German tourist can visit a Portuguese doctor while on vacation and be able to access their complete medical history. In the United States, we are not quite there yet, but other OECD countries have deployed a fully functional national medical record. In Australia, ‘My Health Record’, even allows the patient, to upload their fitness and other consumer medical data to their electronic patient record (EPR) from consumer devices like an Apple Watch or an iPhone. The technological enablement of healthcare has helped to contain costs and to drive provider efficiency by removing the need for duplicate tests and providing information at each physician’s fingertips. AI-based diagnostics is leading to targeted rather than broad treatments, this in turn leads to improved patient outcomes and reduced morbidity and mortality. However, digital transformation has come at a cost.
The fortress citadel of healthcare payers, providers and life sciences organizations is no longer able to secure healthcare data as it once did. That data is now extensively shared with patients, used for research to help drive better pharmaceuticals, healthcare tools and applications. This has greatly expanded the threat surface and healthcare data now spreads far beyond the walled confines of a doctor’s office or a hospital. Web portals where patients can check their insurance coverage, make appointments with providers, review test results, or chat with a physician are now widespread. So too are mobile health applications and a ubiquitous rise in the use of medical wearable sensors such as a Fitbit or an Apple Watch. These monitor patient activity, pulse and heart rate, and no doubt many other things in versions yet to be released. The medical data on all of us is steadily increasing. So too is the aggregate largely de-identified medical dataset used for training of artificial intelligence (AI).
Indeed, rising use of AI based machine learning (ML) is helping to drive clinical decision support and evidence-based medicine. AI has facilitated much safer low-dose radiological imaging and is driving the development of personalized medicine. But AI requires vast amounts of data for model development and training and so presents risks if not properly secured alongside its obvious benefits.
Healthcare IoT (HIoT) and the rise of the Internet of Medical Things (IoMT)
The same is true for medical devices and other healthcare IoT which are growing each year at a staggering
16% compound growth rate. These are connected to medical networks, communicate directly with critical healthcare IT systems such as the EMR and create, store, or transmit large amounts of PHI.
Without even considering their alarmingly rapid growth, these systems all present a huge cybersecurity risk. This is because most were never designed with security in mind. Nor have most been able to be patched when security vulnerabilities are discovered in their underlying operating code. What’s more, many have an amortized life span measured in decades rather than years as an inexpensive Windows PC might be, so these IoT systems will be with us for many years to come.
HIoT includes an array of typically large diagnosis machines – CT, X-Ray, PET, MRI, ultrasound; treatment systems such as ventilators, infusion pumps, defibrillators, radiotherapy, and chemotherapy devices; and a multitude of systems for patient monitoring and management. They also include a rising use of pharmacy and surgical robotic systems, as well as hospital building management systems for managing HVAC which provides hospitals with negative airflow to contain pandemic disease and clean rooms for surgery. These systems include a wide array of laboratories, CCTV, elevators, door locks, and other building systems critical to hospital workflow and safety.
The trouble is that most HIoT devices were built with very narrow design parameters, so they lack the hardware to run newer operating systems, or the storage to support a patched application if that increases the size of the application footprint. Many manufacturers refuse to spend money on developing or testing patches or security fixes because that cost was never built into their business model. Instead, they tell their customers to purchase a newer more secure device, even though there may be many years left on the amortization schedule of the existing system - a device which probably works perfectly, other than to present security risks to the medical network and safety risks to patients. Hospitals and their clinical engineering and cybersecurity teams are faced with the prospect in such cases of retiring early, perhaps millions of dollars in capital assets, patching these devices outside of vendor warranties, or implementing compensating security controls that will pass audit and allow the continued use of these devices till they can be fully written off. None of these options were until recently easy or appealing to healthcare leaders.
Medical devices are connected to the medical network on one side, and often a patient on the other side. They present one of the greatest patient safety and cybersecurity risks of all innovative new healthcare technology. They also present an open back door to hackers with the skills to compromise these simple devices.
Cybersecurity Risk
As healthcare data continues to become ever more valuable, its theft and sale on the dark web can command high prices. So too is the rising value of cyber-extortion where hospitals and other healthcare providers are held to ransom by mafia-like criminals. A closed hospital is one unable to treat patients in-need, and this has major implications for patient morbidity and mortality as well as to the community served by a ransomed hospital. Consequently, and because of lack of preparedness and under-funding in cybersecurity resiliency, healthcare providers tend to pay ransoms at a rate far higher than other industries and this is fueling the growth of an extortion industry that targets healthcare.
All of these factors - digital transformation, growth of AI, rapid expansion of HIoT / IoMT, and shortsightedness by healthcare executives and their government overseers responsible for fueling ransomware are all leading to declining security as the rapid pace of adoption for new healthcare technology far outpaces the cybersecurity needed to keep patients safe and hospitals secure.
Cybersecurity can be a very effective enabler of new riskier opportunities for patients and their care teams to engage together via technologies. But without a corresponding improvement in cybersecurity, new technologies just add risk to an already highly risky industry.
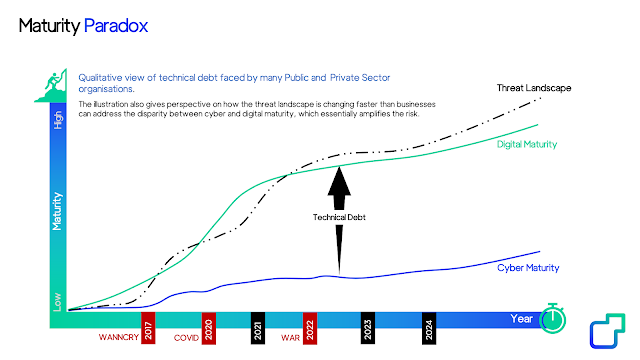
As we continue to introduce new technology to hospitals, so the digital maturity of health IT is outpacing the cybersecurity maturity of healthcare providers, and this leads to a technical debt, gaps which adversaries are easily willing and able to exploit and monetize.
This is the Maturity Paradox.
"Health care has traditionally underinvested in information technology," claims Dr.
John Halamka, chief information officer of Beth Israel Deaconess Medical Center in Boston. Halamka, who has been a CIO since the 1990s, says just a decade ago, pretty much all health records were paper. Then, in a period of a few years, hospitals switched to electronic records. But the security of digital health data has not kept up with its growth. Other industries, like financial services and the federal government,
have devoted more than 12 percent of their IT budgets to cybersecurity. Health care averages
just half that.